Firewalls help monitor traffic and prevent unauthorized accesses based on security rules installed as required. In addition to blocking bad traffic, the firewall also blocks malware from infecting users' computers. Therefore, the firewall is considered the first line of defense of the network security system in every enterprise.
There are 7 popular types of firewalls today
Firewalls are classified based on server or network-based. Some firewall devices also provide functions such as a virtual private network (VPN) or a dynamic host configuration protocol (DHCP).
1. Firewall filters packets
The system will create a checkpoint for the packet to be passed back and forth between computers. Packets are filtered according to source and destination protocol, IP address, destination port, and other external information without opening the packet to examine the content.
If the packet does not meet the test criteria, it will be blocked. These types of firewalls do not consume a lot of resources. However, they are ineffective when compared to firewalls that offer more testing.
2. Circuit Firewall
Circuit firewalls are extremely resourced intensive. They work by verifying the TCP (Transmission Control Protocol), which is designed to ensure session packets are sent from an authenticator.
However, this type of firewall does not self-check the package. Therefore, if a packet contains malware but has a suitable TCP handshake protocol, it still passes the filter.
3. Application Layer Firewall /Layer 7
Proxy firewalls are located at the application layer, between network resources and your system. These types of firewalls are distributed through the cloud or other proxy systems. The proxy firewall controls both the packet and the TCP handshake protocol. In addition, it can also check packages more in-depth to make sure there isn't any malware.
The main advantage of an application layer firewall is that it can understand specific applications and protocols, including hypertext transfer protocol (HTTP), domain name system (DNS), or file transfer protocol (FTP). ).
4. Firewall checks the status
The state-checking firewall is a combination of the TCP handshake protocol and the packet-filtering firewall to ensure greater security. However, this type of firewall slows down the transmission of packets.
5. Cloud Firewall
The main advantage of a cloud-based firewall is that it is very easy to scale with your organization. A cloud firewall is also known as a firewall in service (FaaS). It works the same way as a proxy firewall.
6. Hardware Firewall
This type of firewall needs to be deployed through a physical device that acts as a traffic router, helping to check for traffic requests and packets before they are connected. to your server system.
7. Software firewall
It is a type of firewall installed on a local system instead of having to deploy separate hardware or cloud-based. Software firewalls help in defense by separating separate network endpoints from each other.
How to effectively configure and manage the firewall?
1. Make sure your firewall is safe
• Turn off simple network management protocol (SNMP)
• Rename, disable or delete any of the default user accounts and modify all your default passwords
• Set up additional administrator accounts based on the responsibility when the firewall has more than one administrator.
2. Create the corresponding firewall zones and IP addresses
When setting up multiple zones, the network will be more secure. You must define which assets to protect in order to plan the network structure and location of the networks.
After you've designed a secure network structure and created the right IP address structure, you need to be prepared to re-architect the firewall zones and to allocate them to different types of firewalls.
3. Create an access control list
After setting up the appropriate network zones and firewall allocations, you need to determine what traffic to go in and out of each zone, through the access control list (ACL). You need to use both outgoing and incoming ACLs for each interface to allow inbound and outbound traffic only for each zone.
4. Configure the firewall as required
Your firewall acts as an intrusion prevention system (IPS), network time protocol (NTP), DHCP, etc., you can configure the services you require and turn off all services. The supplement is not related to you.
You need to reference the PCI DSS requirements and meet the requirements of 10.2 through 10.3 of the PCI DSS in order to properly configure your firewall and report it to your logging server.
5. Check firewall configuration
You need to check your firewall to make sure that your firewall is working properly, check both your penetration history and vulnerability scan history, and always make a backup of your firewall configuration.
6. Control the firewall regularly
• Perform a vulnerability scan
• Keep track of diary
• Regularly review firewall rules
• Stay up to date on firmware
• Document progress
Tips for configuring firewall effectively
-
Perform standard regulatory tasks such as NIST, PCI DSS, ISO and NERC
-
Make changes to your firewall configuration regularly
-
Block traffic by default and monitor user access
-
Establish and use only secure connections
-
Streamline configuration changes and eliminate configuration vulnerabilities
-
Continuously check your firewall configuration
-
Record all configuration changes in real-time
-
Have a well-defined firewall change management plan
-
Examine the impact of changing the firewall policy
-
Clean up and optimize the firewall rule base
-
Regularly update the firewall software
-
Centralized firewall management for firewalls of many vendors
Experience the VNETWORK Cloud WAF firewall
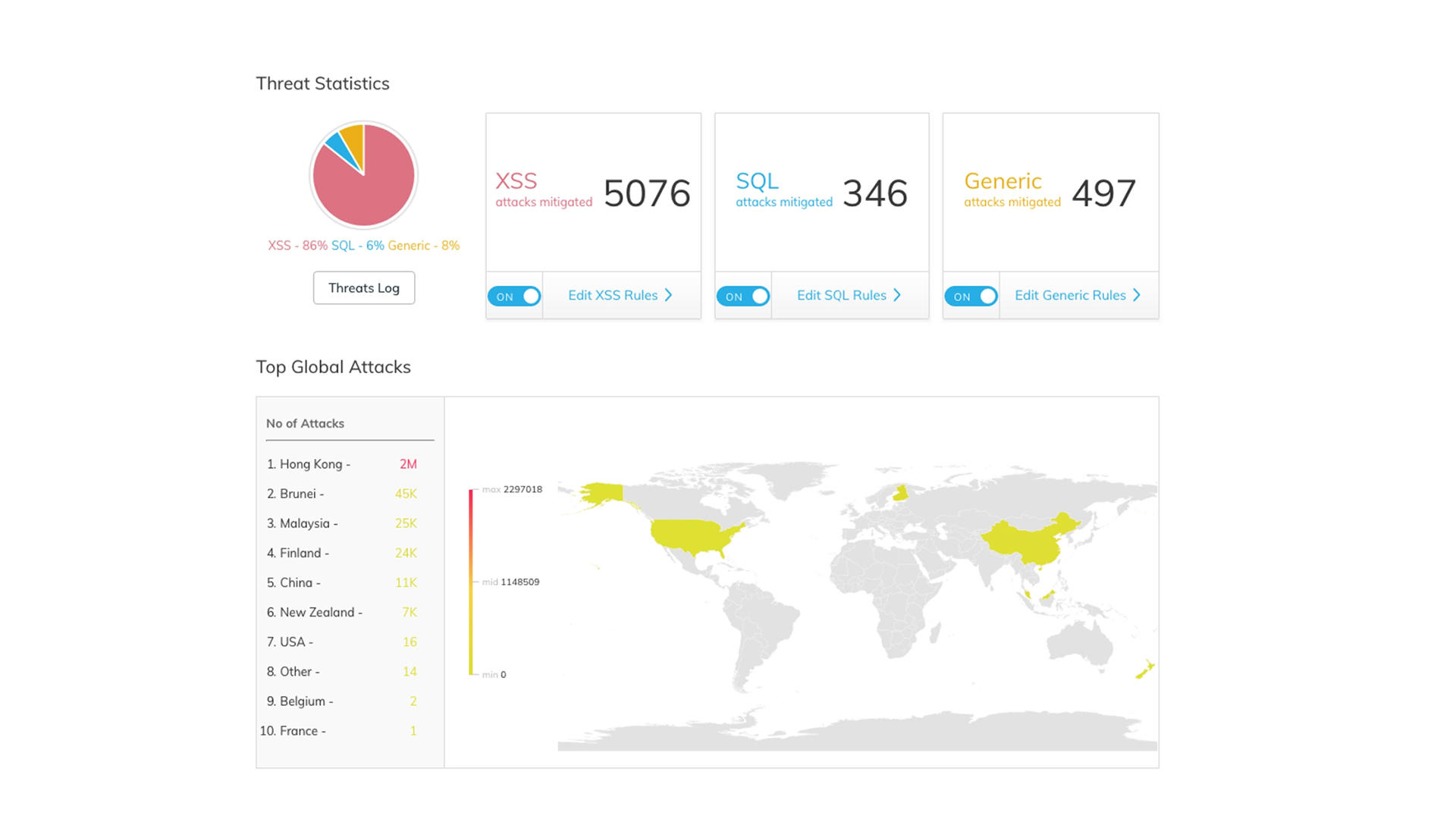
You have more time to experience website security service in 7 days, protecting your web server from dangerous cyber attacks with AI security technology (artificial intelligence).
Cloud WAF VNIS is built on a cloud platform, easily expanding the infrastructure when needed. Effective security capabilities of VNIS are trusted by large enterprises (POPS, PURPOSE, PRIME, LADIPAGE,...)
Call the hotline now: (028) 7306 8789 or live chat for 24/7 support.
