The Internet Domain Name System (DNS - Domain Name System) was first invented in 1983, older than the World Wide Web. Therefore, the protection of DNS services is not only important but also a must for every business.
Status of DNS attacks
The 3 largest DNS DDoS attacks in recorded history are as follows:
-
Attack on the DNS root server in 2002.
-
Attack on Spamhaus - an anti-spam nonprofit, 2013.
-
Attack against Dyn - a company that controls most of the DNS infrastructure, 2016.
This explosion of DNS DDoS attacks is a prime example of the importance of DNS protection. So, how can companies protect themselves against cyberattacks of similar magnitude? Let’s find out with VNETWORK through the following article.
How DNS works and the importance of DNS Anti DDoS
DNS can be understood as the phone book on the internet: it is a tree-structured database that stores a list of domain names and converts them to IP addresses - Internet Protocol.

Here’s how DNS resolves a fully qualified domain name (FQDN) by labels and suffixes: 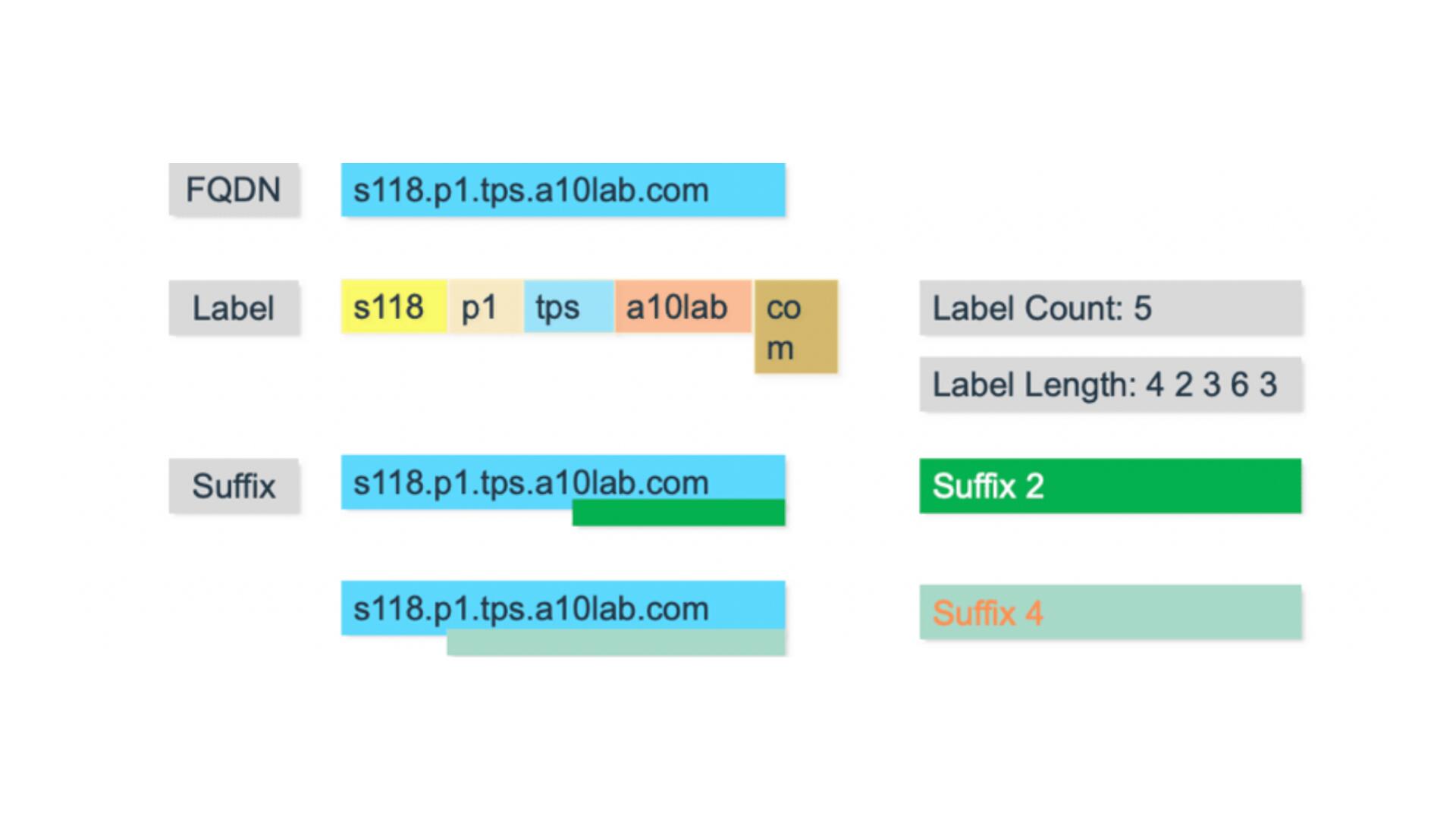
The 3 main reasons why businesses need to put the importance of DNS Anti DDoS on top are:
-
DNS is easy to exploit because of its open nature.
-
Every Web or App application must use DNS, so these applications will be vulnerable to network attacks.
-
DNS attacks often have a wide scope and easily cause a lot of damage to the enterprise’s infrastructure.
How do DNS DDoS attacks happen?
DDoS is one of the most popular cyberattack weapons of cybercriminals worldwide. DDoS attacks often use multiple compromised systems to bring down the target. Therefore, a DDoS attack is considered to be the most devastating type of attack. It affects the most important business need, which is the continuity of websites and applications.

DDoS attacks can be performed either directly or in response. Direct attacks using botnets include compromised IoT devices, computers, or servers. These botnets then target the DNS infrastructure with a large number of queries or packets. This can be done using a real or fake IP address.
Responsive DDoS attacks happen when an attacker spoofs a victim’s IP address - usually a botnet - and spreads it across millions of application servers exposed on the internet. Those servers, including the DNS resolver, then respond to those unauthenticated requests with large responses. Each small request will then be amplified by DNS resolvers up to 54 times the original size.
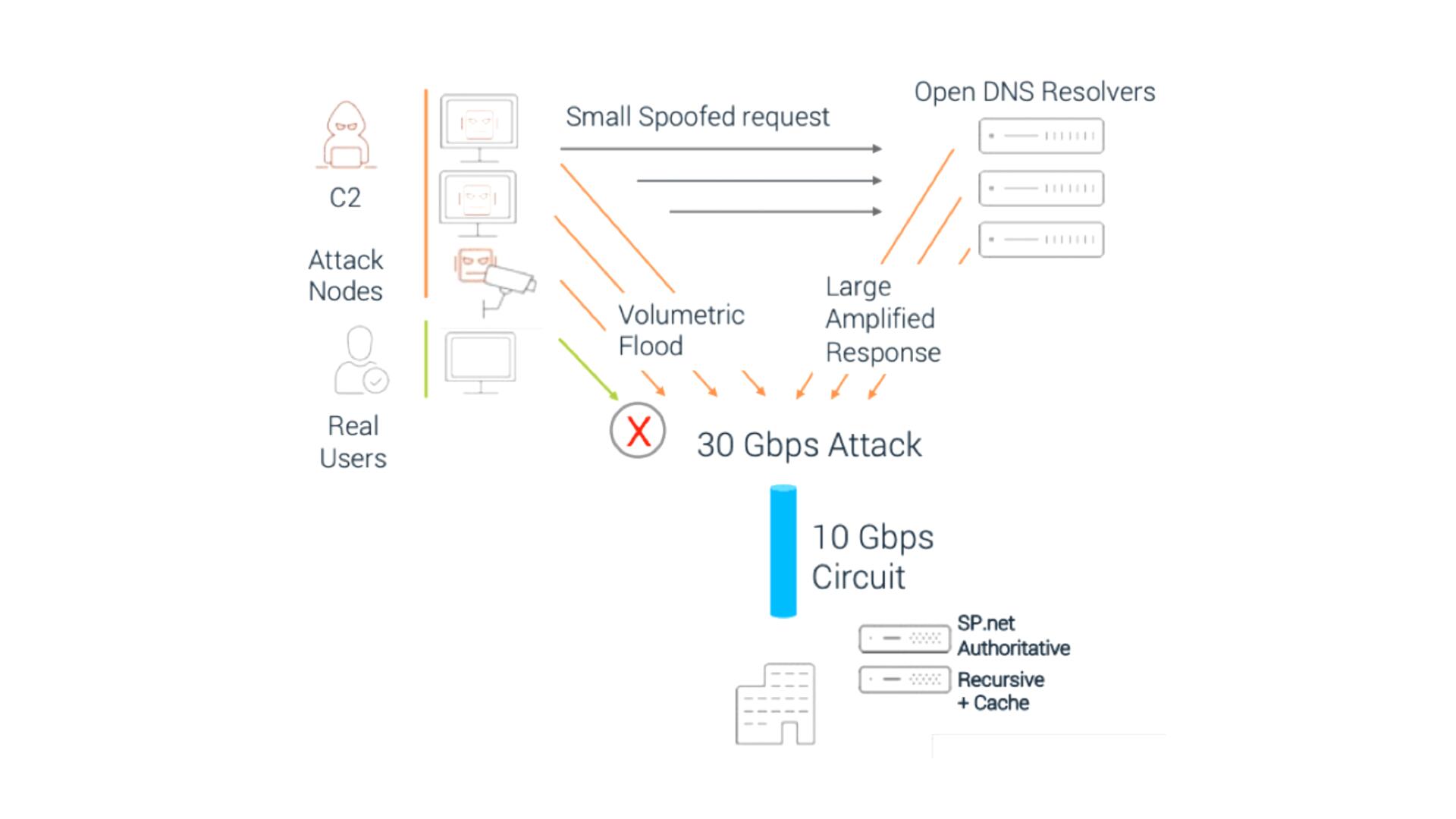
Whether it is direct or reactive attacks, the target of the attack is different. Typically, DNS application attacks also have different purposes as follows:
- Water torture : Also known as pseudo-random subdomain attacks, these attacks bombard DNS resolvers with legitimate domains followed by random labels, forcing DNS to work harder.
- NXDomain : By repeatedly requesting non-existent domains (NXDomains), attackers overload the DNS server and resolver.
- Query flood : Sends loads of queries that flood either the DNS resolver or the authentication server.
- Malformed DNS queries : These types of queries force DNS to complete additional processes and use additional resources.
- Amplify DNS responses : Force DNS to always look for and listen for queries, making it an ideal target for feedback attacks.
DDoS attacks in general can also use strategies like:
- Transmission Control Protocol (TCP SYN flood).
- Internet Control Message Protocol/User Datagram Protocol (ICMP / UDP flood).
- Non-DNS reflection amplification (e.g. NTP, SSDP, etc.).
- Packet anomaly.
Unfortunately, the DNS server responds to <i>everything</i>, whether ping, UDP, or TCP. This makes DNS particularly vulnerable to any type of attack, whether DNS-based or non-DNS attacks.
How to effectively Anti DDoS DNS
There are 2 goals of Anti-DDoS systems:
-
Ensure the availability of services to legitimate users.
-
Ensure IT infrastructure and services are up and running.
If goal #2 is not accomplished, then goal #1 cannot be accomplished either. Therefore, both goals are equally important.
A good Anti-DDoS system will reduce false positives and false negatives. False positives lead to legitimate users being blocked, and false negatives can cause a real DDoS attack to bypass the security layer of the system.
In most anti-DDoS solutions, traffic identification is prioritized, to avoid website congestion or disruption.

As shown in the image above, the traffic filters removed the incorrect traffic. This means legitimate users will be dropped along with malicious traffic.
To avoid this, a DDoS defense system must be able to distinguish between legitimate and illegal users. Currently, several intelligent Anti-DDoS solutions are capable of multi-DDoS detection and mitigation, including escalation mitigation, zero-day attack pattern recognition (ZAPR), and even sophisticated DDoS attacks.
Some ways to protect DNS from DDoS are as follows:
- Drop malformed DNS queries
- Drop non-DNS request to UDP port 53
- Drop DNS ANY request
- Identify reflex amplification attacks
- Limit too many queries per request
- Eliminate abusive FQDN structure or record types
- Authentication requester to prevent forgery
- Monitor NXDomain response from the requester
- Find out the required FQDN to prevent spoofed pseudo-random subdomains
- Initiate roaming to allow only real domains when attacked
- Limit total queries to protected DNS servers
These defenses can prevent many types of DNS DDoS attacks by hackers today.

If you have any questions about DNS security from DDoS, please immediately contact VNETWORK experts for answers.
